Protect Yourself Against Phishing, Win Apple Watch
Learn best practices for fighting phishing during Cybersecurity Month

Bill McCraw was scrolling through his email one August afternoon when he received a message with an alarming subject line: “I Recorded You.”
 The email claimed his computer was infected with malware – malicious software – and that someone spied on him through his webcam.
The email claimed his computer was infected with malware – malicious software – and that someone spied on him through his webcam.
McCraw noticed the message referenced a password he doesn’t use, was also sent to someone without a duke.edu email address and included lengthy links to websites containing dozens of letters and numbers.
“It became obvious pretty quickly that this was spam,” said McCraw, a staff architect for Duke Facilities Management. “I reported it to my colleague at IT in case other people got the same message.”
The message McCraw received was an email extortion attack, in which someone demands money for private information they claim to have accessed.
With Cybersecurity Awareness Month in October, Duke IT professionals are urging staff, faculty and students to #ThinkSecure to avoid falling for cybercrime. During the special campaign, “Security 2020: Protecting Yourself and Your Data in a New Threat Landscape,” staff, faculty and students can participate in webinars and other online activities to spot and report suspicious activity.
“Vigilance is one of the best defenses we can have in protecting ourselves from phishing attacks,” said Cara Bonnett, senior analyst for Duke’s Information Technology Security Office. “Emails manage to slip by our defense systems, so the faster you alert us to attacks or possible breaches in security, the quicker we can act to putting a stop to it.”
As part of the campaign, employees and students who watch a 10-minute “Introduction to Phishing” module on the Duke Security Education Platform, a new portal for easy access to cybersecurity training. All Duke users who complete “Introduction to Phishing” are entered into a drawing to win an Apple Watch.
The Duke Security Education Platform contains 20 other cybersecurity modules from Proofpoint, a service Duke uses to protect against malicious email links and attachments. If you complete four of these other modules on the platform, you’ll be entered into a second drawing for a swag bag, which includes a “#ThinkSecure” T-shirt and other security-related items.
 In addition to the self-directed activities, Duke IT staff will present “Learn IT @ Lunch” live webinars about “Working Securely from Home … with Children” on Oct. 14 and “Security 2020: Protecting Yourself and Your Data in a Changing Threat Landscape” on Oct. 28.
In addition to the self-directed activities, Duke IT staff will present “Learn IT @ Lunch” live webinars about “Working Securely from Home … with Children” on Oct. 14 and “Security 2020: Protecting Yourself and Your Data in a Changing Threat Landscape” on Oct. 28.
Bonnett said that higher education and health care remain top targets for cyber attackers who attempt to gain access to research and health data and personal information and perpetrate financial fraud or disrupt operations.
Using Proofpoint, Duke blocks the vast majority of emails containing spam, phishing attempts and malware. According to Duke’s IT Security Office, about 95 million emails were sent to Duke email addresses in August of this year. About 61 million of them were spam or phishing attempts and blocked.
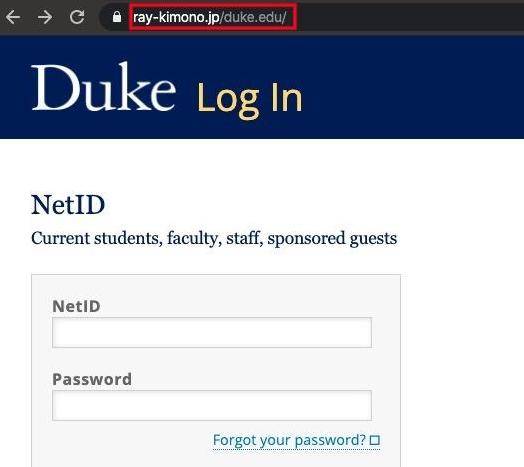
 To avoid phishing attacks through email, Bonnett said one trick is to hover over links to see the website address. The destination should appear, and if it doesn’t match the link, it’s fraudulent. Misspellings, poor grammar and messages demanding something urgently or threateningly should all be red flags.
To avoid phishing attacks through email, Bonnett said one trick is to hover over links to see the website address. The destination should appear, and if it doesn’t match the link, it’s fraudulent. Misspellings, poor grammar and messages demanding something urgently or threateningly should all be red flags.
“We are all busy. We all get a lot of emails,” Bonnett said. “Take a moment to review your messages before clicking on them or responding. It’s better to be safe than sorry.”
Got something you would like for us to cover? Send ideas, shout-outs and photographs through our story idea form or write working@duke.edu.