Phishing Attack Underscores Value of Digital Security
Heading into Cybersecurity Awareness Month in October, an encounter with hackers offers reminder of threats

Late on a Thursday night last month, Duke IT Security Office Senior Manager Nick Tripp was still at work and on the phone. On the other end of the call was a stranger with an eastern European accent, typing in the information Tripp gave him.
 “He was all business, straight to the point, kind of like an annoyed tech support person,” Tripp said. “And as soon as he got what he wanted from me, he hung up. Not as much as a ‘Thank you.’”
“He was all business, straight to the point, kind of like an annoyed tech support person,” Tripp said. “And as soon as he got what he wanted from me, he hung up. Not as much as a ‘Thank you.’”
The person Tripp was speaking to was part of an active phishing attack that, at that moment, had seized control of several Duke email accounts and posed a serious threat to Duke’s IT security. Tripp was playing along with the phish, providing fake information so he could learn more about the hackers and figure out what they were after.
“It was annoying to have to speak with this person who is keeping you at work at 11 o’clock on a Thursday night,” Tripp said. “You just want to say ‘Hey, could you just stop?’”
October is National Cybersecurity Awareness month, offering users at Duke a chance to brush up on safe online behaviors and learn how they play a key role safeguarding digital assets.
Last month’s phishing attack, which saw hackers briefly make inroads through Duke’s email system, provided a real-life example of the threats that exist online, and how individual community members who prioritize cybersecurity can keep hackers from doing real damage.
“It was not a fun few days for anybody, but we could clearly see that people were out there telling us, and telling their entire departments, that something was happening,” said Shelly Clark Epps, Senior Director of Cyber Risk for the Duke Health Security Office. “That speaks to the way that we have tried to activate the entire Duke community to think about security. It could have been much worse than it was.”
 The attack popped onto the radar of Duke’s IT security teams around 11:30 a.m. on Thursday, September 13 as hundreds of Duke email users began forwarding suspicious emails to the security@duke.edu email address and hitting the “Report a Phish” button on Duke’s Outlook email tool.
The attack popped onto the radar of Duke’s IT security teams around 11:30 a.m. on Thursday, September 13 as hundreds of Duke email users began forwarding suspicious emails to the security@duke.edu email address and hitting the “Report a Phish” button on Duke’s Outlook email tool.
The volume of the reports, and the fact that thousands of the suspicious emails were coming from the same valid Duke email account, which hackers had gained control of, made the situation especially concerning.
“As soon as we realized what was happening, we locked the compromised account to cut off the attacker’s ability to send anything more,” Epps said. “And then, the attacker realized it and we saw new accounts, which they had compromised, start sending out new rounds of emails.”
Over the course of Thursday, a response team featuring IT security staff and service desk members from the Duke Office of Information Technology and Duke Health Technology Solutions, discovered and locked six Duke email accounts which hackers had compromised. Another hacked email began sending phishing attempts a few days later, and was quickly locked.
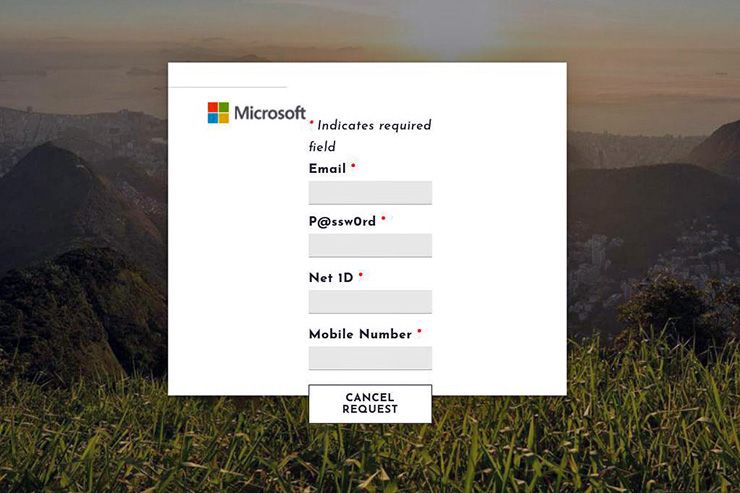 The first rounds of suspicious emails early Thursday claimed to be from Duke, alerting the recipient that their email account would be deleted unless they visited a website and entered their username and password. If recipients followed through with the request, they’d eventually be contacted by the hackers, who would ask them to read the multi-factor authentication codes sent to users’ phones when the hackers tried to log into the users’ email.
The first rounds of suspicious emails early Thursday claimed to be from Duke, alerting the recipient that their email account would be deleted unless they visited a website and entered their username and password. If recipients followed through with the request, they’d eventually be contacted by the hackers, who would ask them to read the multi-factor authentication codes sent to users’ phones when the hackers tried to log into the users’ email.
Later rounds of suspicious emails used offers of attractive jobs to try to obtain valuable data, such as Social Security numbers and banking information.
“We’re not going to catch these people and we’re not going to be able to stop these kind of attacks, but what we can do is slow them down and limit the impact they can have,” Tripp said.
While Duke’s IT security teams are still studying the attack and exploring ways to strengthen defenses against future ones, the saga underscores the importance of a few proven security practices.
- If you receive an email that looks suspicious, use the “Report a Phish Button” to alert Duke’s IT security experts or forward it to security@duke.edu. On first day of the attack, hundreds of users did this, helping Duke’s IT security teams respond quickly. “Initially, we were really excited about the overwhelming response, we were very excited to see that our activated sensor network was working,” Epps said.
- Do not share your passwords or your multifactor authentication codes with anyone. “Duke personnel will never ask you for your passwords or your multi-factor codes,” Tripp said. “If someone is asking for either of those things from you on the phone or in an email, they’re not from Duke.”
- Multifactor authentication remains an effective tool for securing accounts. And Duke OIT offers tools to make using it easier. Duo is a service which allows you to use multifactor authentication easily on your devices, such as smart phones, even when not connected to the Internet. Meanwhile, with Duke Unlock, Duke community members can use features on their personal devices, such as their PIN, face ID or fingerprint, to easily log into Duke sites.
Send story ideas, shout-outs and photographs through our story idea form or write working@duke.edu.