Q&A: How Can Duke Stay Safe from Ransomware?
Duke University Chief Information Security Officer Richard Biever explains a pressing malware threat

In his role as Duke University Chief Information Security Officer Richard Biever, the campus IT Security Office along with the Duke University Health System Chief Information Security Officer Randy Arvay and the DUHS ISO are tasked with protecting Duke from malicious attacks, including ransomware, a type of cyberattack that can cripple digital infrastructure, disrupt operations and cost millions of dollars.
Ransomware is a strain of malware that threatens to encrypt, publish, corrupt or block data, essentially holding it hostage, until a ransom can be paid. Recently, a ransomware attack forced Howard University to briefly cancel classes. Earlier this year, ransomware forced the Colonial Pipeline to pause operations, causing a gas shortage in much of the southeast. And last year, the IT system of Durham’s city government was paralyzed by a ransomware attack.
“It’s easy money,” Biever said. “The idea is, why would hackers go after individuals for hundreds of dollars when you can go after bigger targets and get millions?”
Biever and his colleagues in the Duke IT Security Office work hard protecting Duke’s digital systems from malware attacks like ransomware. Ransomware attacks often start with phishing emails. Last month, Duke received roughly 103 million emails, with roughly 69 million messages automatically blocked. However, in the 39 million delivered, there is still a chance that some phishing messages could make it through.
Staff, faculty and students all play a role in security efforts by not falling for and reporting potential phishing attempts that could lead to malware. With Cyber Security Awareness Month in October, Working@Duke talked with Biever to gain an understanding of the threat of ransomware and how community members can defend against it.
What does ransomware do?
Biever said that, like any type of malware, ransomware can find its way onto a computer when a user opens a compromised file, often disguised as a document from a common program such as Microsoft Word, Excel, or Adobe (pdf). And while the scam can start small, with one infected device, ransomware can quickly become a big problem since it is designed to rapidly spread through networks, infecting devices and data.
 And like a timebomb, the ransomware is designed to encrypt all data on devices it accesses at once, paralyzing entire computer systems and disrupting their operations. When that happens, the only way for an organization to reverse the encryption and regain access to their computer systems is to pay a ransom – often in the millions – to the people behind the cyberattacks.
And like a timebomb, the ransomware is designed to encrypt all data on devices it accesses at once, paralyzing entire computer systems and disrupting their operations. When that happens, the only way for an organization to reverse the encryption and regain access to their computer systems is to pay a ransom – often in the millions – to the people behind the cyberattacks.
“They look for vulnerabilities in the system and then use that as an entry point to deploy the initial malware,” Biever said. “The more they spread, the more systems that have access to. And once they hit a certain point, they turn on the encryption.”
Why is ransomware a threat?
Ransomware has been around for decades, but its earliest incarnations focused on infecting individual computers, forcing users to pay to regain access to data. But in recent years, hackers have gained access to more powerful tools that make it easier to have malware from one computer infect entire networks.
 “They’ve gotten a taste for how ambitious they can be, so they’re swinging for the fences,” Biever said.
“They’ve gotten a taste for how ambitious they can be, so they’re swinging for the fences,” Biever said.
Biever said that’s led to ransomware becoming a much more attractive approach for more sophisticated cybercriminals looking to make larger sums of money, and for foreign governments trying to destabilize the nation’s infrastructure and financial systems.
According to a report from digital security firm Checkpoints, there were 93 percent more ransomware attacks in the first half of 2021 than the same period last year.
Biever said the increase is mainly due to more personal and professional communication happening online and often on the same devices.
“You can see situations now where what you’re doing from a personal perspective – going to a website, checking email, or something like that – could end up in a negative action that gets transferred to the business or professional side,” Biever said. “That becomes the doorway for something to spread further into your business network.”
Why are higher education institutions and health organizations targets?
Health care organizations have been a popular target for ransomware attacks in recent years. In 2021, the U.S. Department of Health and Human Services reported that 34 percent of health care organizations have been the target of ransomware attacks in the previous year.
Biever said Duke’s academic, research and health care operations make it an inviting target for ransomware since the areas have sensitive data.
“Higher education is well known for being focused on collaboration and the sharing of information,” Biever said. “We’re all about encouraging academic and research pursuits. This could present opportunities for attackers to send email messages looking like they’re coming from potential collaborators or to apply social engineering techniques to try to take advantage of the openness and trusting attitude that a lot of us have.
What role can faculty, staff and students play in protecting Duke from ransomware?
Biever and his team in the IT Security Office, and their counterparts in Duke University Health System, fight ransomware cyberattacks on multiple fronts. They stay on top of the latest threats and vulnerabilities and make sure to send crucial updates and patches to Duke managed devices. They also employee security tools and methods to help identify and respond to potential attacks.
 But as Biever points out, even with these security measures, Duke students, staff and faculty can still help. He said it’s important to install updates – most install automatically when you restart your computer – when they are recommended. These often feature security patches that remedy gaps that hackers can exploit.
But as Biever points out, even with these security measures, Duke students, staff and faculty can still help. He said it’s important to install updates – most install automatically when you restart your computer – when they are recommended. These often feature security patches that remedy gaps that hackers can exploit.
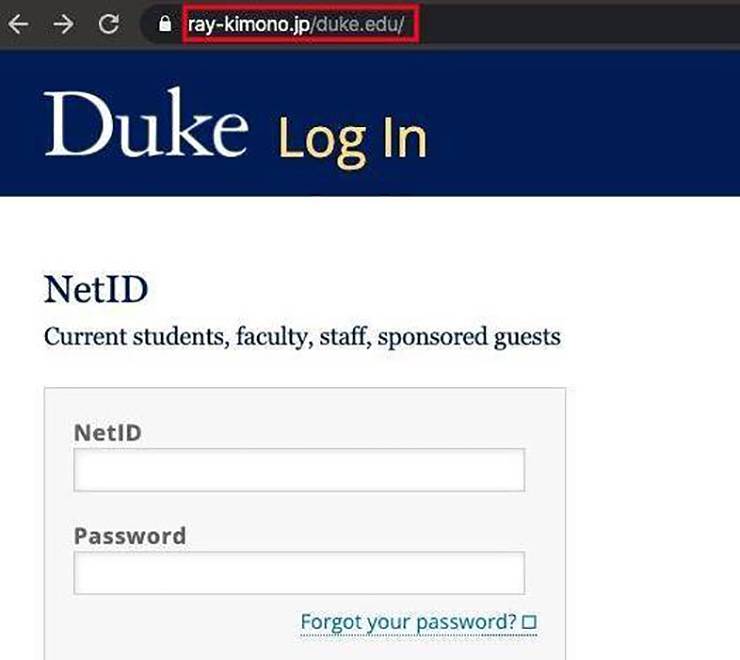
And Biever stressed the importance of being a discerning email user by not clicking on attachments unless you’re sure what it is, that it’s coming from a trusted source, and reporting suspicious emails to the Duke IT Security Office by clicking on the “Report Phish to Duke” button on Outlook email accounts.
To sharpen the online acumen of a team, managers can request to take part in monthly or quarterly drills in which Duke security experts send teams simulated phishing emails. Duke University Health System employees are automatically enrolled in the program.
And with October being Cybersecurity Awareness Month, Duke’s Office of Information Technology (OIT) is running the Duke Security Challenge, a game which offers Duke students, staff and faculty a chance to win prizes while learning about cybersecurity.
At noon on October 27, OIT will also offer a free Learn IT @ Lunch webinar, “Security 2021: Protecting Yourself and Your Data in a Changing Threat Landscape.”
“There are a number of things you can do to protect yourself,” Biever said. “But, one of the biggest things our community can do is staying aware and it something seems off, don’t click on it. Don’t investigate it yourself. Tell somebody about it.”
For a deep dive into the threat posed by ransomware, check out this webinar from a recent edition of the Virtual Security Academy from Duke’s IT Security Office.
Send story ideas, shout-outs and photographs through our story idea form or write working@duke.edu.