How Not to Fall for a Phishing Scam
In observance of cybersecurity awareness month, Duke’s IT Security watchdogs offer advice on what to look for in scam emails

Like many of her colleagues at Duke, Alexis Sharp is constantly connected to email, so she knows when something doesn’t look right.
That quality came in handy recently when she received an email from a supposed friend and fellow Duke employee.
“It said, ‘Please click on this link, I need you to sign this document for me,’” said Sharp, a clinical research coordinator with Duke Heart Center’s Clinical Research Unit. “I thought it looked strange even though it was sent from her email address.”
Sharp didn’t click the link. Instead, she reached out to her friend and asked if she’d just sent an email.
“She said ‘no, definitely not,’” Sharp said. “That’s when I forwarded it on to the IT folks to work their magic.”
According to Duke’s IT Security Office, about 199 million emails were sent to Duke email addresses in July of this year. About 166 million were marked as spam or phishing attempts and blocked. But no matter how strong the defenses, dubious emails still get through, meaning the most important line of defense is you.
Users of Duke’s email system, such as Sharp, play a crucial role in alerting Duke’s IT Security Office of threats.
“The hacking attempts are getting more and more sophisticated and we rely on the community as an early-warning detection system,” said Cara Bonnett, a senior IT Analyst with Duke University’s IT Security Office.
According to a recent report from Verizon Data Breach Investigations, around ninety percent of the nation’s reported data breaches are the result of phishing.
As part of National Cybersecurity Awareness Month in October, take a quiz to test your phishing detection skills. All Duke community members who take the quiz will be entered in a drawing to win an Apple Watch Series 3.
And check out these examples and tips on how to spot phishing attempts.
Links and email addresses can be faked

Scammers can steal your information by getting you to click on links to sites that expose your computer to risk or download files that do damage. Hackers do this by disguising links to look like addresses the user would consider safe. The tactic is called “spoofing.”
An easy way to see if the link is legitimate is to use your mouse to hover over it. The destination should appear and, if it doesn’t match the link, it’s fraudulent.
Email addresses can be disguised as well, making it look like the message is coming from a sender you know.
The best was to combat these tactics is to simply trust your gut. If something about the email seems off, don’t click on anything and alert Duke’s IT Security Office.
“It’s really important because we’re dealing with confidential, secure information here at Duke that we don’t want outsiders to be privy to,” Sharp said. “I always take everything with a grain of salt and ask if that’s something I really want to be clicking on. It may have bad consequences, not just for myself, but for Duke overall.”
Spelling errors and poor grammar are warning signs
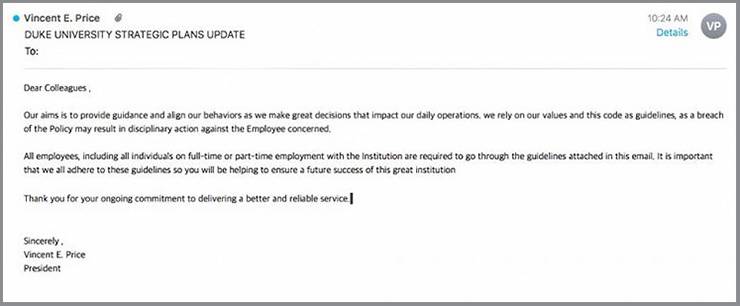
Odds are, the people you connect with through your Duke account are going to have a connection to higher education or health care. So, messages received shouldn’t be riddled with blatant errors and iffy grammar.
Scammers aren’t traditionally known as excellent writers, so if you’re reading an email that’s filled with mistakes – especially like the one above, purporting to be from Duke University President Vincent Price – get your guard up.
Urgency is a red flag
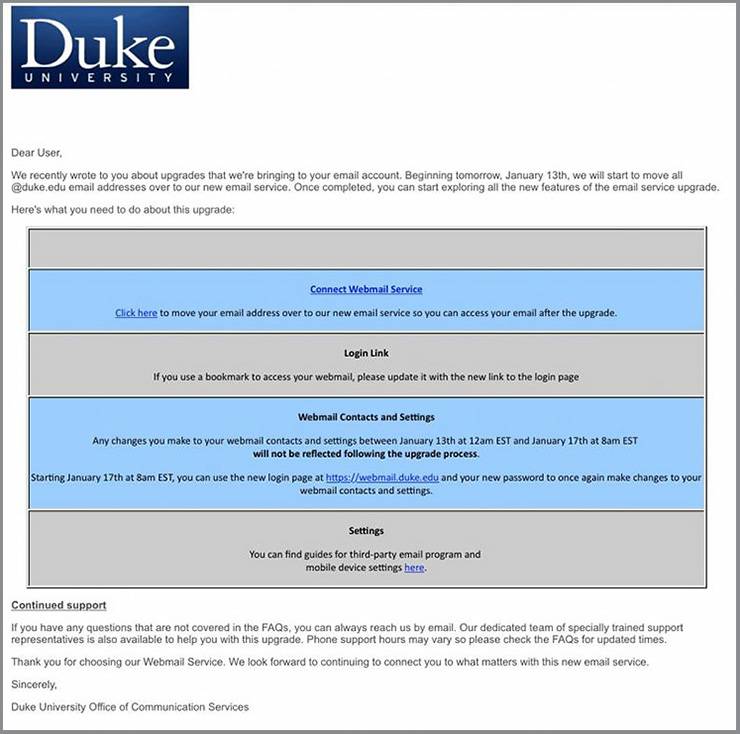
A common tactic of scammers is to send an email with urgent instructions. If you receive something you weren’t expecting requesting you change a password, click a link or download something right away, odds are good it’s not legitimate.
“I’m generally aware that something that’s asking you to follow a link and login, and it’s something you weren’t expecting, it’s suspicious, you should pay extra attention to it,” said Ara Wilson, an associate professor of Gender, Sexuality & Feminist Studies, who’s reported a handful of phishing attempts to the Duke IT Security Office.
Be careful with attachments

Hackers have long relied on attachments in email to implant malware or viruses on a victim’s computer. But there are other ways attachments can lead to trouble.
In recent months, Duke’s IT Security Office has seen an uptick in convincing emails using spoofed addresses and containing attachments. When downloaded, the attachments will ask for a password in order to be opened. Once entered that password becomes compromised.
“Generally, don’t open it if it’s something you’re not expecting,” said Bonnett, the senior IT Analyst with Duke University’s IT Security Office. “It’s more than just, ‘Think before you click.’ It’s often just ‘don’t click.’ It’s safer that way.”
Get to know the Duke login page
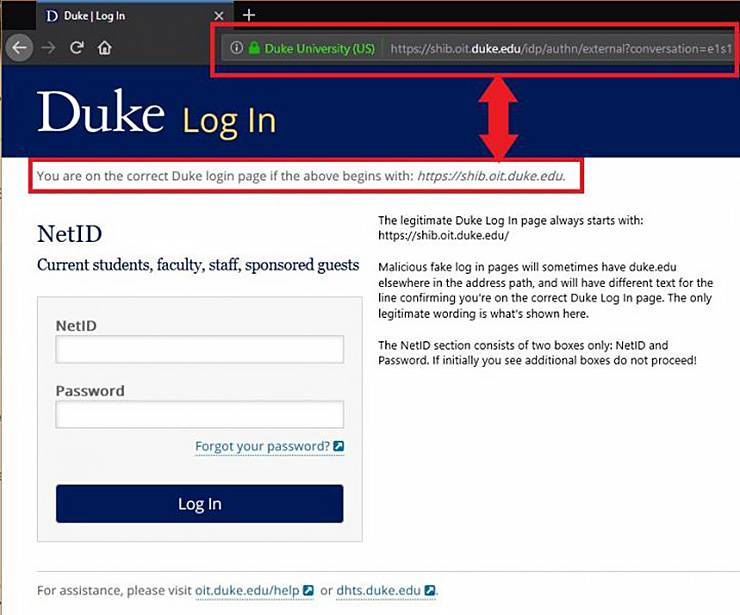
As the gateway to protected parts of Duke’s online presence, the Duke log in page is a prime target for hackers. Duke’s IT Security Office has seen instances when scammers have reconstructed the site, complete with convincing logos and layout, in an effort to gain users NetID and password information.
That’s why it’s important to be familiar with the page and make sure the URL is correct before you enter any information.
“Anyone can be phished under the right circumstances,” Bonnett said. “We’re all busy. We get a lot of email in and out. And the sophistication of the attacks is always increasing.”
If you receive a suspicious email, let Duke’s IT Security Office know about it here or by email security@duke.edu.
Throughout October, Duke’s IT Security Office will share tips and resources to help staff, faculty and students protect their digital security.
Have a story idea or news to share? Share it with Working@Duke.